When you need an answer from tech support, from me, or from an overseas support desk, there are some basics that will make it easier to get an actual answer. As in any writing, we have to anticipate the questions that will result from what is written, and just go ahead and answer them in advance. Here’s how you can best communicate with techies. Including me.
Tell us Where the Issue is
While I may know what computer you are most likely to be using, many of you have two, or an office full of them. Specify which computer. If it has been a while, or you’re emailing those support desks in Asia, also mention what version of Windows is in use.
“It doesn’t work”
“It doesn’t work.” doesn’t say anything for a tech; we already knew that because the message arrived. The pronoun ‘it’ provides no clue what doesn’t work. Second, “doesn’t work” could mean any of these:
- Nothing happens
- Fails, with an error message
- Something else happens
- Menu or button isn’t where it was
- Some other program takes over
Instead, tell what you tried to do, and then what happens.
What you Tried to do
So say what you are trying to do. There’s no need to be technical about it:
- Tried to create an envelope in Word 2013
- Trying to send an email in Thunderbird
- Couldn’t edit font size in WordPerfect
- Tried to run my specialty database
- Tried to open QuickBooks
The program name is important. And the ‘Internet’ or ‘AOL’ is a web site, not a program. The program name usually shows up at the top-left of your open program.
What Happened
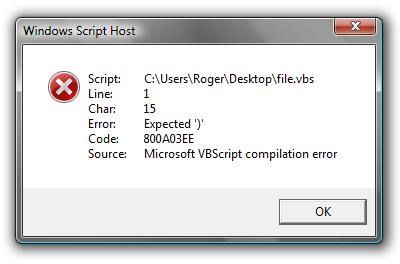
And that’s where you include a picture, because trying to describe an error message is usually not going to work. They’re mostly too long, and they don’t stay on-screen while you’re typing that email. So a screen capture is the best approach. Refresher course–here’s how to do that:
The Windows shortcut to capture the top window is alt-Print Screen, sometimes shown as PrtScrn on your keyboard–it’s usually at the top-right. Nothing appears to happen when you press those keys–that’s OK. Go to uour email in Outlook or Thunderbird, and paste in the image; Control-v will generally work.
Or if you’re using webmail or Gmail, open Microsoft Paint, or Word, or WordPerfect, and use paste (ctrl-v) to add the image. Save that file, and attach it to your email.
There’s also ctrl-PrtScrn. It works, but will take a picture of the entire screen, not just the top window. If you have multiple monitors, it will capture all of them. Mostly, alt-PrtScrn is easier, as it will only capture whichever window is on top of your desktop.
Some screens can’t be captured, usually the infamous Windows BSOD, or ‘blue screen of death’. For those, write down the error number, usually something like “0xc0000007e”, and send that. Or use your phone to take a picture and email it.
One Topic
Emails asking techs for answers should have just one topic. The overseas tech will normally glance at a message, and paste in canned response number 17, whatever that could be, because they saw a word that mentioned something vaguely 17-ish. That might not be the important answer you needed, or even useful. The best tech questions are about just how to fix one issue.
That even applies for me. I will send a quick short answer if you ask one question. If you also ask a question that needs research, or a price quote, it will take a lot longer.