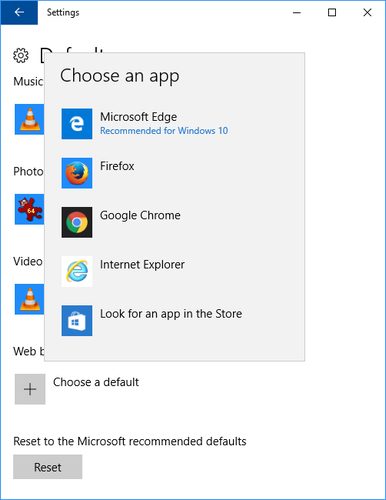
A reprint from the PC410 Security Newsletter:
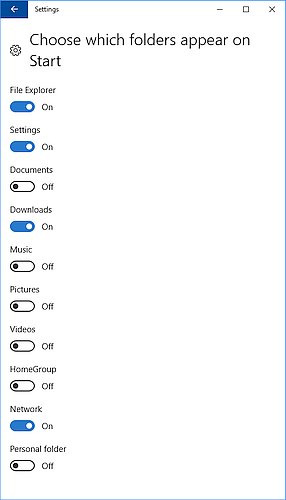
Windows 10 removes the Documents and Pictures shortcuts from the Start menu. You can have them back, or choose to show Music, Videos, or the Network. Go to Settings, Personalization, Start, click on “Choose which folders appear on Start”. Turn on (or off) any of the folders in the list. If you turn a folder off, you can still get to it from File Explorer (the yellow file folder icon in the taskbar), or by pressing Start and typing in the folder name to search for it.