And today’s hoax email is a social engineering attack, arriving as a fake web charge DOC file. It wants me to open a DOC file and enable macros, and no, I didn’t do that.
Subject: Re: filetiger.com charge on my card
WTF is this $263.48 charge on my card?
I never ordered anything from filetiger.com.
I have attached a screenshot of my statement.
WTF is this about?Thank you
Attachment: ss_filetiger.com_47155.doc
OK, I know what the transaction sizes are for my FileTiger file management software on my FileTiger.com site, and if there was a $263 site license sale for a product that sells for $9.90, I would have been notified when it happened. So it’s suspicious. There’s no signature, and the sending address has the email address as the name, like this:
abe@b.com <abe@b.com>
(I won’t show the original email addresses, as they’re both fake and variable, and likely stolen from an infected computer’s address book.)
Next, there are carbon copies to three other addresses, on three different domains. One of them is at Ford.com. Really. Another goes to a domain with no web site.
And, of course, it’s all blandly generic. The domain name is there, and it was sent to the email address associated with that domain, publicly available from the records at my domain registrar.
OK, well, I’m clearly not going to open a suspicious doc file in Word; it’s a stupid thing to do; Word has auto-run macros, and there are constant patches to force Word to ask permission before launching the macros, and workarounds for the bad guys to avoid that permission, especially if your version of Word is not the newest edition. Instead, I open it in the vastly-safer WordPerfect, which won’t run embedded macros without permission, ever, and couldn’t run a Microsoft Word macro in any case. This image is inside: (Note that the logo for Office is wrong–it’s not a Microsoft message.)
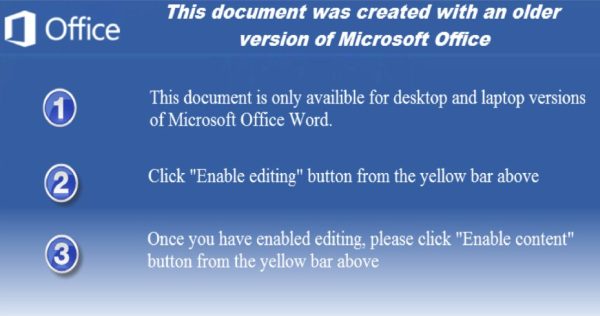
Wow. Brazen. It asks me to “Enable editing” and then to “Enable content”.
OK, next, I take the file and submit it VirusTotal.com, which runs it against (currently) 55 antivirus products. I did this only 10 minutes after it arrived, so there are only 3 ‘infected’ diagnosis, but it’s clearly evil:
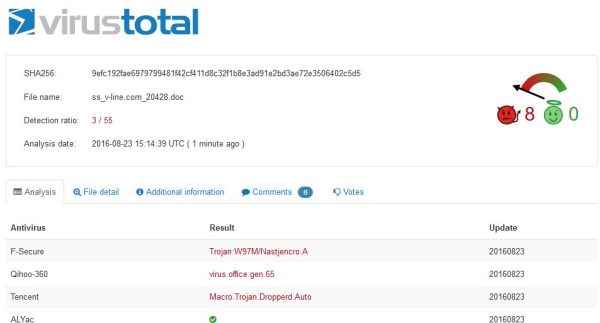
Note that VirusTotal recognized the file with another domain name, but scanned the same day as I received it, one minute ago, in fact.
I also looked inside the file with a pure text editor; there are a lot of totally random phrases in there, so it’s probably being re-generated regularly to stay ahead of AV detection software.
As always, the defense against these social-engineering attacks is the same: Don’t open attachments you didn’t ask for.
UPDATE, Later in the same day:
Apparently, I’m ripping off a lot people and should expect chargebacks. I have just received an identical message, but now from an email address in Japan. The filename has changed to “ss_filetiger.com_197472.doc”, and VirusTotal says it’s a different file, but it’s now recognized as malware by 6 of the 54 scanning programs, although it’s still not detected by the AV software I’m running locally. In other words, AV can’t keep up.