There’s a picture in the Windows 10 Search bar. This started after the May 2022 Windows Update, and so far, I’ve seen either owls, a swimming turtle, tennis, a tea cup with what might be mint, or a purple flower and a bee. No idea what this kiddy cartoon is called other than looking very much look a toolbar added by malware. Or a BHO, also known as a browser helper object. Maybe a widget, a gadget? Maybe it’s a distant relative of the old Clippy, the Talking Paper Clip from Office ’97? Microsoft has used so many names for extra screen clutter over the years that this is clearly a Whatever. Yes, whatever that is.
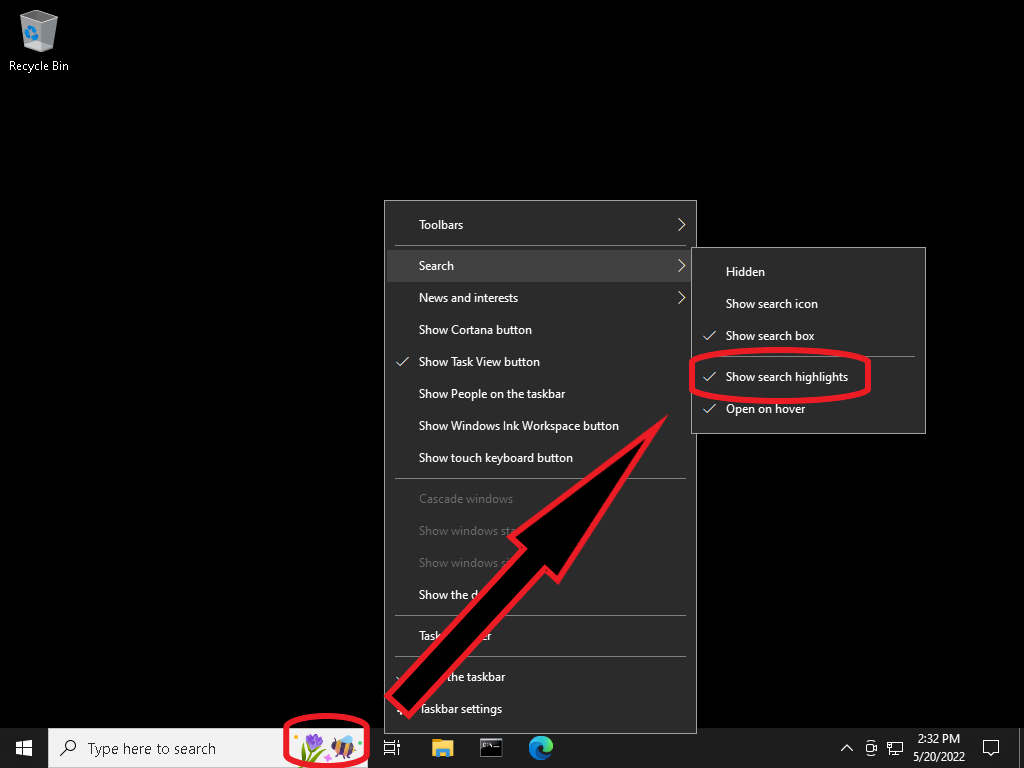
Here’s how to turn off the Whatever: Right-click the Search box, and the menu will pop up as below. Uncheck ‘Show search highlights’. Done.
If anybody knows what that setting changes beyond adding cartoons to the bar, let me know and I’ll update this.
Updated May 21st with the tea cup. And on May 22nd with the Tennis image. And so on…
